2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
With the rapid evolution of blockchain technology, the need for robust security measures has never been more critical. In 2024 alone, $4.1 billion was lost due to DeFi hacks, highlighting vulnerabilities across various platforms. This alarming trend raises the question: How can we ensure the security of our digital assets? Here’s where the
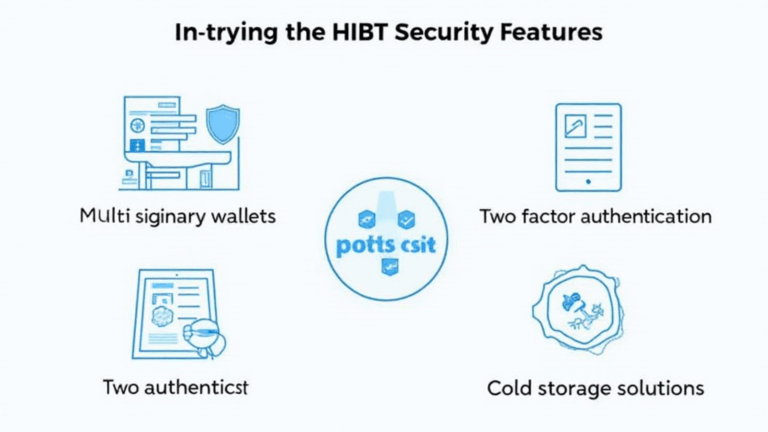
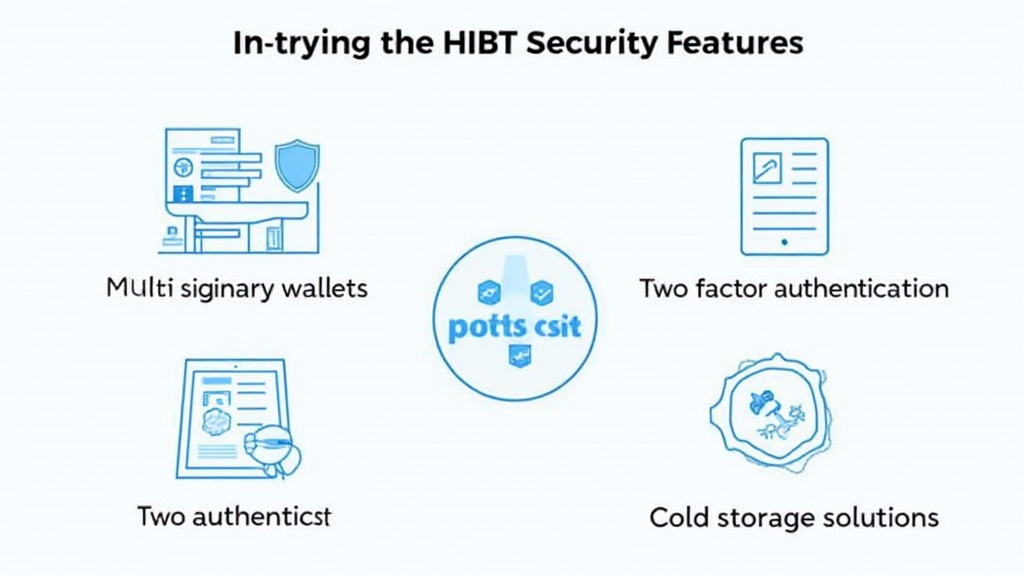
1. Understanding HiBT Security Features
The security features of HiBT are designed to provide enhanced protection for users’ digital assets. Let’s explore the fundamental components that underpin these features:
ong>Multi-Signature Wallets: ong> These provide an added layer of approval for transactions, ensuring that no single party has control.ong>Two-Factor Authentication (2FA): ong> A crucial feature, requiring not only a password but also a one-time code sent to a user’s mobile device.ong>Regular Security Audits: ong> Engaging third-party auditors to examine the system for vulnerabilities.ong>Cold Storage Solutions: ong> Keeping the bulk of funds offline protects them from online threats.
[Insert a relevant image with the ALT text: “HiBT security features infographic”]
2. The Importance of Compliance in Blockchain Security
In the wake of regulatory changes, maintaining compliance has become a cornerstone of security strategy. HiBT security features not only address technical aspects but are also aligned with legal requirements to ensure user protection.
- Adherence to
ong>GDPR ong>: Protecting user data and privacy. - Mandatory KYC Regulations: Verifying user identity minimizes fraud risk.
- Regular Reporting: Transparency through detailed reporting on security audits.
In Vietnam, the demand for compliant platforms is surging. According to recent market analysis, compliance-focused platforms have seen a
3. Consensus Mechanisms and Their Vulnerabilities
In essence, consensus mechanisms are critical for blockchain security. However, they are not without their vulnerabilities.
ong>Proof of Work (PoW): ong> Susceptible to 51% attacks which could lead to double-spending.ong>Proof of Stake (PoS): ong> Potential for centralization if a few stakeholders control a majority of the assets.
Implementing
4. Smart Contract Audit Strategies
Smart contracts are at the heart of many blockchain projects, which means auditing them is essential. Here’s how HiBT integrates effective audit strategies:
ong>Automated Code Analysis: ong> Utilizing tools to scan for vulnerabilities.ong>Formal Verification: ong> Mathematically proving the correctness of smart contract algorithms.
So, how to audit smart contracts effectively? By implementing these strategies, platforms can avoid costly exploits and ensure user trust.
[Insert a relevant image with the ALT text: “Smart contract audit process”]
5. The Role of User Education in Security
No security strategy is complete without user awareness. Educating users about potential risks and how to protect their assets is critical. Here are some effective educational strategies:
- Creating intuitive guides on using security features like 2FA.
- Offering webinars to discuss the importance of security in the crypto space.
Engaging users can significantly lower the risk of common security issues, such as phishing attacks.
Conclusion: The Future of Blockchain Security
As we venture into 2025, the importance of implementing HiBT security features cannot be overstated. With the changing landscape of regulations and increasing cyber threats, platforms like ristomejidebitcoin are taking the necessary steps to ensure that user funds are safe. Ultimately, the combination of cutting-edge technology, compliance, and user education will pave the way for a secure future in the blockchain space.
In summary, adopting these
[Insert a relevant image with the ALT text: “Blockchain security future trends”]