Essential HiBT Verification Steps for Cryptocurrency Security
As cryptocurrencies continue to gain traction globally, loss incidents have skyrocketed, with a staggering
Understanding HiBT Verification Steps
The
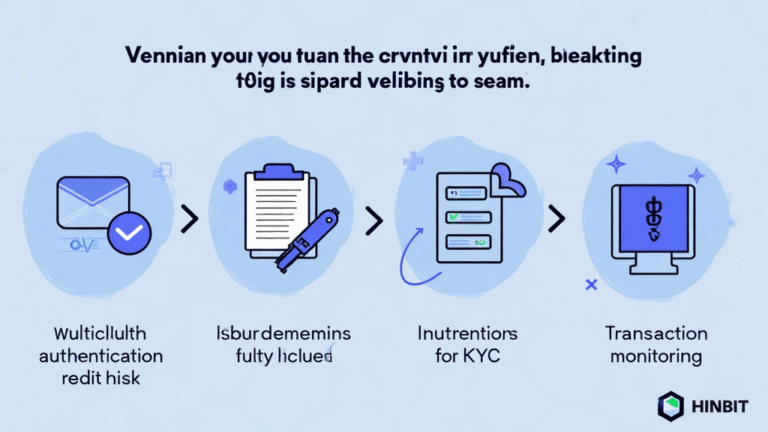
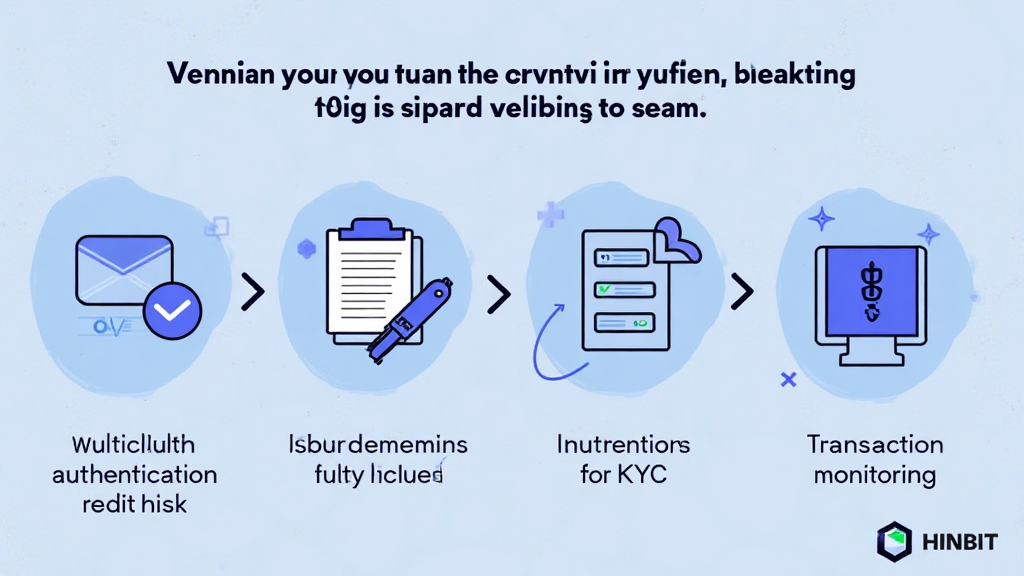
ong>Multi-Factor Authentication (MFA): ong> Before initiating any transaction, platforms must ensure that users authenticate their identities through multiple channels, like SMS, email, or authenticator apps.ong>Know Your Customer (KYC): ong> Collecting and verifying identification details helps reduce the risk of money laundering and other illegal activities.ong>Regular Security Audits: ong> Platforms must conduct audits to identify vulnerabilities in their systems, employing third-party evaluations for increased credibility.ong>Transaction Monitoring: ong> Implement software capable of real-time monitoring and analysis of all transactions for suspicious activities.
The Importance of Compliance with HiBT Standards
Following HiBT verification steps ensures adherence to international regulations, which is vital for operating in diverse markets, including Vietnam. The
How HiBT Steps Enhance User Experience
Let’s break this down: when users feel secure, they engage more freely with cryptocurrency platforms. For instance, in Vietnam, the user growth rate in the crypto market is steadily increasing. Providing robust verification steps serves not only to protect users but also enhances overall engagement.
Real-World Application of HiBT Verification Steps
Consider a scenario where a user attempts to transfer 5 BTC. With proper verification steps in place, the transaction must meet multiple criteria before approval:
- Verify the user’s identity through MFA.
- Check the history of transactions for any red flags.
- Assess the receiving wallet for known associations with fraud.
This systematic approach significantly reduces risks, ensuring a safer ecosystem for digital transactions.
Data Transparency and User Trust
According to recent studies, platforms that disclose their security measures see a
Conclusion: Elevating Your Crypto Security Strategy
Implementing the
For more insights on enhancing your crypto platform’s security and compliance, be sure to visit hibt.com.
In conclusion, thorough understanding and implementation of
**Author: John Doe,** a cybersecurity analyst with over 15 published papers on blockchain security protocols and has led audits for prominent crypto projects.